| Oracle® Label Security Administrator's Guide 10g Release 1 (10.1) Part Number B10774-01 |
|
|
View PDF |
| Oracle® Label Security Administrator's Guide 10g Release 1 (10.1) Part Number B10774-01 |
|
|
View PDF |
This chapter explains how to create an Oracle Label Security policy. It contains these sections:
To create and implement an Oracle Label Security policy, you perform the following tasks, which are described in the next few chapters:
Create a policy by defining:
To do this in Oracle Policy Manager, you can use the Create Policy icon or the Policy property sheet.
Alternatively, you can use the SA_SYSDBA.CREATE_POLICY command line procedure.
Define the levels, compartments, and groups that form the components of the new policy's labels.
To do this in Oracle Policy Manager, go to Oracle Label Security Policies--> policyname-->Labels and use the Labels property sheet.
Alternatively, you can use the SA_COMPONENTS package on the command line.
Specify the set of valid labels to support the policy. From all the possible combinations of levels, compartments, and groups, you must define labels that can be assigned to data.
Alternatively, applications that need to create data labels dynamically at runtime can use the TO_DATA_LABEL function.
|
Note: When Oracle Label Security is installed to work with Oracle Internet Directory (OID), dynamic label generation is not allowed, because labels are managed centrally in OID, using olsadmintool commands. (See Appendix B, "Command-line Tools for Label Security Using Oracle Internet Directory".) Therefore, when Oracle Label Security is directory-enabled, this function, TO_DATA_LABEL, is not available and will generate an error message if used. |
To use Oracle Policy Manager to define labels that can be assigned to data, go to Oracle Label Security Policies--> policyname-->Labels and use the Labels property sheet.
Protect individual database tables and schemas by applying the policy to them. In the process, you can customize the level of enforcement of the policy for each table and schema, to reflect your application security requirements.
To do this with Oracle Policy Manager, go to Oracle Label Security Policies--> policyname-->Protected Objects. Select either Schemas or Tables, and use the corresponding property sheet.
Alternatively, you can use the SA_POLICY_ADMIN package.
For individual users, define the authorizations that each person will use for session access. If users do not have appropriate authorizations, they cannot access protected data.
You can optionally assign special privileges that particular users need to do their job. Note that Oracle Label Security privileges may only be necessary to perform special job functions.
To do this with Oracle Policy Manager, go to Oracle Label Security Policies--> policyname-->Authorizations-->Users and use the User property sheet.
Alternatively, you can use the SA_POLICY_ADMIN package.
Create any necessary stored trusted program units, and set their labels and privileges.
To do this with Oracle Policy Manager, go to Oracle Label Security Policies--> policyname-->Authorizations-->Program Units and use the User property sheet.
Alternatively, you can use the SA_USER_ADMIN package.
Configure monitoring of the administrative tasks and use of privileges, if desired.
To do this with Oracle Policy Manager, go to Oracle Label Security Policies--> policyname-->Auditing and use the Auditing tab page of the Policy property sheet.
To do this with Oracle Policy Manager, go to Oracle Label Security Policies-->Authorizations-->Users--> username. Use the Auditing tab page of the User property sheet.
Alternatively, you can use the SA_AUDIT_ADMIN package to set auditing options for policies, users, and program units.
You can manage the administration of an Oracle Label Security policy in various ways. The policy_DBA role is created when you create a new policy, and every individual who needs to perform administrative functions must be granted this role. However, you can grant EXECUTE privileges on the administrative packages to different users, so that each administrator can be restricted to a subset of the administrative functions.
For example, you could grant EXECUTE privilege on SA_COMPONENTS and SA_LABEL_ADMIN to one user or role to manage the label definitions, and grant EXECUTE on SA_USER_ADMIN to a different user or role to manage user labels and privileges. Alternatively, you could grant EXECUTE on all of the administrative packages to the policy_DBA role, so that anyone with the policy_DBA role could perform all of the administrative tasks.
You can perform Oracle Label Security development and administrative tasks using either of two interfaces:
Oracle Label Security packages provide a direct, command-line interface for ease of administration. These include:
For a demonstration showing how to create and develop an Oracle Label Security policy using the supplied packages, refer to the olsdemo.sql file in your ORACLE_HOME/rdbms/demo directory.
You can use Oracle Policy Manager, an extension to Oracle Enterprise Manager, to administer Oracle Label Security. Figure 6-1 is a representative screenshot that illustrates the Oracle Policy Manager interface. Please see the online help for instructions on how to use this graphical user interface.
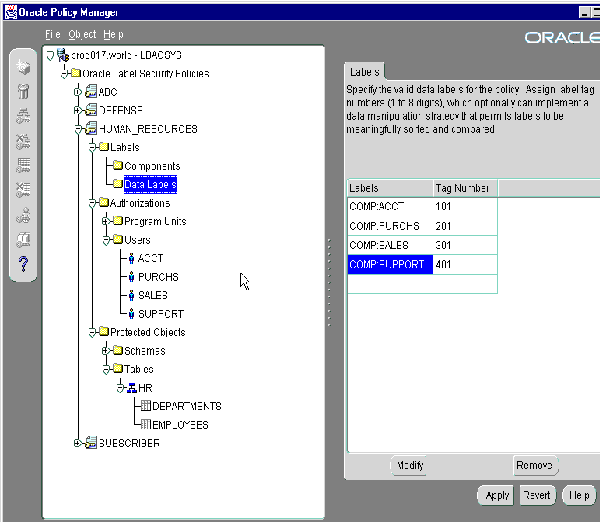
Text description of the illustration opm1test.gif
This section explains how to manage a policy using the SA_SYSDBA package. To do this in Oracle Policy Manager, use the Create Policy icon or the Policy property sheet.
To use the SA_SYSDBA package to create, alter, and drop policies a user must have:
When you create a policy, a role named policy_DBA is automatically created. You can use this role to control the users who are authorized to execute the policy's administrative procedures.
For example, after you have created a human resources policy named HR, an HR_DBA role is automatically created. To use any administrative packages, a user would need to have the HR_DBA role. If Joan is the administrator of the HR policy, and David is the administrator of the FIN policy, then Joan has the HR_DBA role and David has the FIN_DBA role. Each person can only administer the policy for which he or she has the policy_DBA role.
The user who creates the policy is automatically granted the policy_DBA role with the ADMIN option, and can grant the role to others.
Valid characters for all policy specifications include alphanumeric characters and underscores, as well as any valid character from your database character set.
Use the CREATE_POLICY procedure to create a new Oracle Label Security policy, define a policy-specific column name, and specify a set of default policy options.
Syntax:
PROCEDURE CREATE_POLICY ( policy_name IN VARCHAR2, column_name IN VARCHAR2 DEFAULT NULL, default_options IN VARCHAR2 DEFAULT NULL);
See Also:
|
Use the ALTER_POLICY procedure to set and modify policy default options.
Syntax:
PROCEDURE ALTER_POLICY ( policy_name IN VARCHAR2, default_options IN VARCHAR2 DEFAULT NULL);
Use the DISABLE_POLICY procedure to turn off enforcement of a policy, without removing it from the database. The policy is not enforced for all subsequent access to the database.
To disable a policy means that no access control is enforced on the tables and schemas protected by the policy. The administrator can continue to perform administrative operations while the policy is disabled.
Syntax:
PROCEDURE DISABLE_POLICY (policy_name IN VARCHAR2);
| Parameter Name | Parameter Description |
|---|---|
|
policy_name |
Specifies the policy to be disabled |
Normally, a policy should not be disabled in order to manage data. At times, however, an administrator may need to disable a policy in order to perform application debugging tasks. In this case, the database should be run in single-user mode. In a development environment, for example, you may need to observe data processing operations without the policy turned on. When you re-enable the policy, all of the selected enforcement options become effective again.
Use the ENABLE_POLICY procedure to enforce access control on the tables and schemas protected by the policy. A policy is automatically enabled when it is created. After creation or enabling, the policy is enforced for all subsequent access to tables protected by the policy
Syntax:
PROCEDURE ENABLE_POLICY (policy_name IN VARCHAR2);
| Parameter Name | Parameter Description |
|---|---|
|
policy_name |
Specifies the policy to be enabled |
Use the DROP_POLICY procedure to remove the policy and all of its associated user labels and data labels from the database. It purges the policy from the system entirely. You can optionally drop the label column from all tables controlled by the policy.
Syntax:
PROCEDURE DROP_POLICY (policy_name IN VARCHAR2, drop_column BOOLEAN DEFAULT FALSE);
| Parameter Name | Parameter Description |
|---|---|
|
policy_name |
Specifies the policy to be dropped |
|
drop_column |
Indicates that the policy column should be dropped from protected tables (TRUE) |
This package manages the component definitions of an Oracle Label Security label. Each policy defines the components differently. This section contains these topics:
| See Also: |
Chapter 2, "Understanding Data Labels and User Labels" for information about the components "Using Oracle Label Security Views" for information about displaying the label definitions you have set |
Oracle Label Security makes use of overloaded subprogram names. That is, the same name is used for several different procedures whose formal parameters differ in number, order, or datatype family.
For example, you can call the SA_COMPONENTS.ALTER_LEVEL procedure this way:
PROCEDURE ALTER_LEVEL (policy_name IN VARCHAR2, level_num IN INTEGER, new_short_name IN VARCHAR2 DEFAULT NULL, new_long_name IN VARCHAR2 DEFAULT NULL);
or this way:
PROCEDURE ALTER_LEVEL (policy_name IN VARCHAR2, short_name IN VARCHAR2,
new_long_name IN VARCHAR2);
Because the processing in these two procedures is the same, it is logical to give them the same name. PL/SQL determines which of the two procedures is being called by checking their formal parameters. In the preceding example, the version of initialize used by PL/SQL depends on whether you call the procedure with a level_num or short_name parameter.
Use the CREATE_LEVEL procedure to create a level and specify its short name and long name. The numeric values assigned to the level_num determine the sensitivity ranking (that is, a lower number indicates less sensitive data).
Syntax:
PROCEDURE CREATE_LEVEL (policy_name IN VARCHAR2, level_num IN INTEGER, short_name IN VARCHAR2, long_name IN VARCHAR2);
Use the ALTER_LEVEL procedure to change the short name and/or long name associated with a level.
Once they are defined, level numbers cannot be changed. If a level is used in any existing label, then its short name cannot be changed, but its long name can be changed.
Syntax:
PROCEDURE ALTER_LEVEL (policy_name IN VARCHAR2, level_num IN INTEGER, new_short_name IN VARCHAR2 DEFAULT NULL, new_long_name IN VARCHAR2 DEFAULT NULL); PROCEDURE ALTER_LEVEL (policy_name IN VARCHAR2, short_name IN VARCHAR2, new_long_name IN VARCHAR2);
Use the DROP_LEVEL procedure to remove a level. If the level is used in any existing label, it cannot be dropped.
Syntax:
PROCEDURE DROP_LEVEL (policy_name IN VARCHAR2, level_num IN INTEGER); PROCEDURE DROP_LEVEL (policy_name IN VARCHAR2, short_name IN VARCHAR2);
Use the CREATE_COMPARTMENT procedure to create a compartment and specify its short name and long name. The comp_num determines the order in which compartments are listed in the character string representation of labels.
Syntax:
PROCEDURE CREATE_COMPARTMENT (policy_name IN VARCHAR2, comp_num IN INTEGER, short_name IN VARCHAR2, long_name IN VARCHAR2);
Use the ALTER_COMPARTMENT procedure to change the short name and/or long name associated with a compartment.
Once set, the comp_num cannot be changed. If the comp_num is used in any existing label, then its short name cannot be changed, but its long name can be changed.
Syntax:
PROCEDURE ALTER_COMPARTMENT (policy_name IN VARCHAR2, comp_num IN INTEGER, new_short_name IN VARCHAR2 DEFAULT NULL, new_long_name IN VARCHAR2 DEFAULT NULL); PROCEDURE ALTER_COMPARTMENT (policy_name IN VARCHAR2, short_name IN VARCHAR2, new_long_name IN VARCHAR2);
Use the DROP_COMPARTMENT procedure to remove a compartment. If the compartment is used in any existing label, it cannot be dropped.
Syntax:
PROCEDURE DROP_COMPARTMENT (policy_name IN VARCHAR2, comp_num IN INTEGER); PROCEDURE DROP_COMPARTMENT (policy_name IN VARCHAR2, short_name IN VARCHAR2);
Use the CREATE_GROUP procedure to create a group and specify its short name and long name, and optionally a parent group.
Syntax:
PROCEDURE CREATE_GROUP (policy_name IN VARCHAR2, group_num IN INTEGER, short_name IN VARCHAR2, long_name IN VARCHAR2, parent_name IN VARCHAR2 DEFAULT NULL);
Note that the group number affects the order in which groups will be displayed when labels are selected.
Use the ALTER_GROUP procedure to change the short name and/or long name associated with a group.
Once set, the group_num cannot be changed. If the group is used in any existing label, then its short name cannot be changed, but its long name can be changed.
Syntax:
PROCEDURE ALTER_GROUP (policy_name IN VARCHAR2, group_num IN INTEGER, new_short_name IN VARCHAR2 DEFAULT NULL, new_long_name IN VARCHAR2 DEFAULT NULL); PROCEDURE ALTER_GROUP (policy_name IN VARCHAR2, short_name IN VARCHAR2, new_long_name IN VARCHAR2);
The ALTER_GROUP_PARENT procedure changes the parent group associated with a particular group.
Syntax:
PROCEDURE ALTER_GROUP_PARENT (policy_name IN VARCHAR2, group_num IN INTEGER, parent_name IN VARCHAR2); PROCEDURE ALTER_GROUP_PARENT (policy_name IN VARCHAR2, group_num IN INTEGER, parent_num IN INTEGER); PROCEDURE ALTER_GROUP_PARENT (policy_name IN VARCHAR2, short_name IN VARCHAR2, parent_name IN VARCHAR2);
Use the DROP_GROUP procedure to remove a group. If the group is used in existing labels, it cannot be dropped.
Syntax:
PROCEDURE DROP_GROUP (policy_name IN VARCHAR2, group_num IN INTEGER); PROCEDURE DROP_GROUP (policy_name IN VARCHAR2, short_name IN VARCHAR2);
| Parameter Name | Parameter Description |
|---|---|
|
policy_name |
Specifies the policy |
|
group_num |
Specifies the number of an existing group for the policy |
|
short_name |
Specifies the short name of an existing group |
The SA_LABEL_ADMIN package provides an administrative interface to manage the labels used by a policy. To do this, a user must have EXECUTE privilege for the SA_LABEL_ADMIN package and have been granted the policy_DBA role.
This section includes:
Use the SA_LABEL_ADMIN.CREATE_LABEL procedure to create a valid data label. You must manually specify a label tag value from 1 to 8 digits long.
Syntax:
PROCEDURE CREATE_LABEL ( policy_name IN VARCHAR2, label_tag IN INTEGER, label_value IN VARCHAR2, data_label IN BOOLEAN DEFAULT TRUE);
When specifying labels, use the short name of the level, compartment and group.
When you identify valid labels, you specify which of all the possible combinations of levels, compartments, and groups can potentially be used to label data in tables.
|
Note: If you create a new label by using the TO_DATA_LABEL procedure, a system-generated label tag of 10 digits will be generated automatically. However, When Oracle Label Security is installed to work with Oracle Internet Directory (OID), dynamic label generation is not allowed, because labels are managed centrally in OID, using olsadmintool commands. (See Appendix B, "Command-line Tools for Label Security Using Oracle Internet Directory".) Therefore, when Oracle Label Security is directory-enabled, the TO_DATA_LABEL function is not available and will generate an error message if used. |
Use the ALTER_LABEL procedure to change the character string label definition associated with a label tag. Note that the label tag itself cannot be changed.
If you change the character string associated with a label tag, the sensitivity of the data in the rows changes accordingly. For example, if the label character string TS:A with an associated label tag value of 4001 is changed to the label TS:B, then access to the data changes accordingly. This is true even though the label tag value (4001) has not changed. In this way you can change the data's sensitivity without the need to update all the rows.
Note that, when you specify a label to alter, you can refer to it either by its label tag or by its character string value.
Syntax:
PROCEDURE ALTER_LABEL ( policy_name IN VARCHAR2, label_tag IN INTEGER, new_label_value IN VARCHAR2 DEFAULT NULL, new_data_label IN BOOLEAN DEFAULT NULL); PROCEDURE ALTER_LABEL ( policy_name IN VARCHAR2, label_value IN VARCHAR2, new_label_value IN VARCHAR2 DEFAULT NULL, new_data_label IN BOOLEAN DEFAULT NULL);
Use the SA_LABEL_ADMIN.DROP_LABEL procedure to delete a specified policy label. Any subsequent reference to the label (in data rows, or in user or program unit labels) will raise an invalid label error.
Syntax:
PROCEDURE DROP_LABEL ( policy_name IN VARCHAR2, label_tag IN INTEGER); PROCEDURE DROP_LABEL ( policy_name IN VARCHAR2, label_value IN VARCHAR2);
Use this procedure only while setting up labels, prior to data population. If you should inadvertently drop a label that is being used, you can recover by disabling the policy, fixing the problem, and then re-enabling the policy.