| Oracle® Security Overview 10g Release 1 (10.1) Part Number B10777-01 |
|
|
View PDF |
| Oracle® Security Overview 10g Release 1 (10.1) Part Number B10777-01 |
|
|
View PDF |
This chapter introduces the Oracle products and special features that can protect your data using the latest security technology.
Database security entails permitting or denying user actions on the database and the objects within it. Oracle uses schemas and security domains to control access to data and to restrict the use of various database resources. This section describes the many intrinsic security mechanisms of the Oracle database.
For a thorough discussion of these features, see the Oracle documentation set.
Oracle Identity Management is an integrated infrastructure that provides distributed security services for Oracle products and other enterprise applications. The Oracle Identity Management infrastructure includes the following components and capabilities:
In addition to its use of SSL, OC4J, and HTTP Server, Oracle Application Server Certificate Authority has a built-in reliance on SSO and OID. OCA publishes each valid certificate in an OID entry for the DN in use. SSO and other components can rely on these OID entries because OCA removes revoked and expired certificates from OID on a regular basis. The administrator also has the option of configuring OCA to publish its URL through SSO. This configuration choice causes every SSO-authenticated user who lacks a certificate to see the OCA page for requesting one. OCA certificates can be used to authenticate to any Oracle component or to authorize use of any application that is SSO-enabled.
In a typical enterprise application deployment, a single Oracle Identity Management infrastructure is deployed, consisting of multiple server and component instances. Such a configuration provides benefits that include high availability, information localization, and delegated component administration. Each additional application deployed in the enterprise then leverages the shared infrastructure for identity management services. This deployment model has a number of advantages, including:
For more information about planning, deploying, and using the Oracle Identity Management infrastructure, see the Oracle Identity Management Administrator's Guide. Default and recommended configurations, with installation instructions, appear in the Oracle Application Server 10g Installation Guide.
Oracle contains many mechanisms to ensure the integrity of the database, and to provide concurrency, serializability of transactions, and to prevent data corruption. The access control mechanisms that enforce mandatory access control are also used to prevent unauthorized modification and deletion of data by users.
Oracle provides data integrity through the use of declarative entity and referential integrity constraints as defined in the ISO/ANSI SQL standards. Integrity rules are specified declaratively as part of the table definition, and are checked by the database server whenever transactions update, insert, or delete rows in the table. Defining and enforcing these rules in the server ensures that all applications consistently and reliably apply the same rules, which can be maintained centrally. Enforcement in the server also provides performance benefits over programmatic enforcement in the application.
More complex business rules can be enforced through the use of stored procedures and triggers. However, these mechanisms are not normally used to enforce entity, referential, or transaction integrity.
Database integrity mechanisms also guarantee that all steps in a transaction are committed as a complete unit, so that either all parts are committed or all parts are rolled back (transaction integrity).
Entity integrity enforcement guarantees that each row in a table is uniquely identified by non-null values contained in its primary key columns. An example of entity integrity would be ensuring that every employee number in the EMP table is unique.
Referential integrity constraints are used to enforce dependencies and relationships between rows in tables. An example of this occurs when an employee's department number in the EMP table (foreign key) must be a valid department as specified in the DEPT table (primary key). Primary key/foreign key relationships are defined as part of table creation.
Oracle provides user authentication to ensure that the identity of a user, host or client is correctly known. To access a database, a user must supply a valid username and associated password of the database. These prevent unauthorized use. Oracle also provides authorization, to ensure that a user, program, or process receives the appropriate privileges to access an object or set of objects
To prevent unauthorized use of a database username, Oracle provides user validation by several different methods for normal database users. You can perform authentication by:
Further, Oracle Enterprise Edition supports additional modes of authentication:
For simplicity, one method is usually used to authenticate all users of a database. However, Oracle permits use of all methods within the same database instance.
Oracle regulates all user access to data through privileges. It supports the concept of least privilege, which states that users should be granted the least number of privileges necessary to perform their jobs. Oracle enforces this concept by not automatically granting users any direct privileges when they are created. It supports both column-level and row-level privileges. Column-level privileges can be granted directly, and row-level privileges can be granted programmatically or through Oracle Label Security. The highly granular system and object privileges of Oracle enable you to grant users only the specific privileges they need, rather than having to grant them more encompassing privileges.
Oracle has extensive support of roles, to enable administrators to optimally manage users' privileges. Oracle Standard Edition supports
Note that Oracle Enterprise Edition supports additional roles:
Oracle permits selective auditing of user actions to provide accountability. Audit records can also be a useful tool in identification of suspicious user activity. Auditing can be performed at different levels: by user, by statement, by privilege (such as SELECT), and by schema object (such as SELECT FROM EMP).
Oracle9i views and stored program units can add an additional level of security to your system. Views can restrict user access to a predetermined set of rows and columns of a table. Stored program units (such as stored procedures, packages, and triggers) can be used for such purposes as performing a set of related tasks, enforcing complex security authorizations, or restricting certain DML operations.
Among other security technologies, Oracle protects data in eBusiness systems through strong, standards-based encryption. Oracle has supported encryption of network data through Oracle Advanced Security (formerly known as "Secure Network Services", and then "Advanced Networking Option") since Oracle7. Oracle also supports protection of selected data by means of encryption within the database.
To address the need for selective data encryption, Oracle provides a PL/SQL package to encrypt and decrypt stored data. The package, DBMS_OBFUSCATION_TOOLKIT, supports bulk data encryption using the Data Encryption Standard (DES) algorithm, and includes procedures to encrypt and decrypt using DES. In addition to single DES, Oracle's DBMS_OBFUSCATION_TOOLKIT supports triple DES (3DES) encryption, in both two and three key modes, for those who demand the strongest commercial available level of encryption. The toolkit also supports the MD5 secure cryptographic hash to ensure data integrity, and a random number generator for generating secure encryption keys.
Multiple Oracle mechanisms - including resource limits and user profiles, online backup and recovery, and advanced replication - help provide uninterrupted database processing and minimize denial of service in order to support today's on-line transaction processing and decision support environments. Availability encompasses both functionality and performance. Performance and service level objectives can be impacted by the distribution of resources among various applications accessing the database. The Database Resource Manager gives the Oracle database server more control over resource management decisions, and can circumvent problems resulting from inefficient operating system (OS) management and OS resource managers.
Resource limitation and user profile mechanisms prevent "run-away" queries, or more deliberate and malicious manipulation of system resources by a particular user. A user profile is a set of administrator-defined resource limits assigned to a username; through the use of user profiles, Oracle enables the database administrator to define and limit the amount of certain system resource available to a user. System resources that can be limited include:
Through user profiles, Oracle prevents resource hogs from denying service to other users, either inadvertently or maliciously.
Oracle also ensures high availability by providing robust online backup and recovery, so that mission-critical applications are not inhibited by these necessary activities. Oracle provides an integrated method for creating, managing, and restoring backups of a database, providing greater ease of management and administration of the backup and recovery operations, while maintaining superior performance and increased availability of the database. Oracle databases can be backed up on-line, even during periods of peak transaction processing activity. Server-managed backup and recovery improves database administrator productivity as well as simplifying the backup and recovery process. Oracle backup and recovery permits backing up of the entire database, or a subset of the database, in one operation, and minimizes time needed for backup and restore operations by performing automatic parallelization of backups and restores. Oracle backup and recovery also supports sequential I/O devices for output during backup and for input during restore operations. Tape backups are supported in conjunction with vendor-provided tape management systems.
The advanced replication facilities of Oracle can be used to increase the availability of systems by off-loading large scale queries from transaction processing databases. For example, large tables of customer purchasing data may be replicated to customer service databases, so that data-intensive queries do not contend with transactions against the same tables. Advanced replication facilities can also be useful in protecting the availability of a mission-critical database. For example, symmetric replication can replicate an entire database to a failover site should the primary site be unavailable do to a system or network outage. Advanced replication for both read and write access ensures data consistency; refresh groups preserve referential integrity and transaction consistency and the table snapshots of related master tables. For example, customers, orders, order lines are all related, so could be refreshed as a group.
Data partitioning in Oracle is a powerful tool for dramatic improvements in the manageability, performance, and scale of applications deployed using the Oracle data server. Oracle permits range partitioning of tables and multiple partitioning strategies for indexes, providing very large database support, and improves administrative operations. In the real world, media failure, access balancing for performance, and table de-fragmentation are just a few of the areas where partitioning can reduce the impact of a outage or increase availability under high loads.
Oracle with the Partitioning option supports all DML operations in parallel today. In addition, scans of indexes, export and import of table data, and estimating and calculating statistics can also be performed in parallel on individual partitions. Partitions can be loaded individually and in parallel, with or without index pre-creation. Loading, backup, recovery, computing statistics, and import and export are all supported for each partition. These can be performed individually without interfering with operations underway on other partitions. With every operation available on a partition basis, it is possible to have truly dramatic performance improvements.
Real Application Clusters provide very high levels of availability for mission critical applications. In a Real Application Clusters environment, Oracle runs on two or more systems in a cluster, while concurrently accessing a single shared database. In the event of a failure of one of the systems, the surviving systems perform recovery of the failed Oracle instance. This provides some tremendous availability and scalability benefits over simple cold cluster failover.
This section describes Oracle support for proxy authentication.
The OCI proxy authentication feature was initially released in Oracle8i, and enabled a database client to set up, within a single database connection, a number of "lightweight" user sessions, each of which is associated with a different database user.
In Oracle proxy authentication, authentication of the client is supported in the following ways:
In Oracle this feature is designed so that a specific middle tier can be restricted to acting on behalf of a specified set of users. Once the middle tier has authenticated itself to the database, it can establish a lightweight session on behalf of those users without submitting user-specific authentication information such as passwords. Moreover, Oracle can be configured so that a specific middle tier can assume a specific set of database roles when acting at the database on behalf of a specific user. In other words, the database uses both middle tier identity and client user identity when determining what privileges to grant a middle tier acting for a user through a lightweight session.
In Oracle8i the proxy authentication feature was limited to communications to the database that used the Oracle Call Interface (OCI), but Oracle has now extended the feature to Java Database Connectivity (JDBC) access to the database. A middle tier server can now access the Oracle database on behalf of a client user by establishing a lightweight session for that user through JDBC-OCI.
Oracle8i supported proxy authentication for database users authenticated by password only; the password could be passed as an attribute to be verified by the database, or not, depending on an organization's security preferences.
Oracle extends proxy authentication to include additional credential proxy of either the Distinguished Name (DN) or full X.509 certificate to the database. This provides strong, three-tier security by enabling an SSL credential--an X.509 certificate or DN--to be passed to the database for purpose of identifying (but not authenticating) the user. (SSL cannot be used to authenticate a user through multiple tiers, since it is a point-to-point protocol rather than an end-to-end protocol.) For example, a user can authenticate to a middle tier using SSL, the middle tier can extract the DN from the certificate and pass it (or the full certificate) to the database. As an additional benefit, the DN or certificate is available in the lightweight session and the elements contained therein can be used with Virtual Private Database to limit access. For example, an organization could restrict data access based on the Organizational Unit (OU) element in a user certificate presented to the database.
The database can use the DN or certificate to look up a user in Oracle Internet Directory or other LDAP-based directory certified for enterprise user security (an Oracle Advanced Security feature). Integration of proxy authentication with enterprise user security enables the user identity to be maintained throughout all tiers of an application, yet the user need only be created once, in the directory. This also enables enterprise user security to be used in three-tier applications, instead of merely client/server, as was the case with Oracle8i.
Many applications use session pooling to set up a number of sessions that are reused by multiple users. In this context, "application users" are users who are authenticated to the middle tier of an application, but are not known to the database. Oracle supports application user proxy authentication for these types of applications.
In this model, the middle tier passes a client identifier to the database upon session establishment. (The client identifier could be anything that represents the client connecting to the middle tier; a cookie, for example, or an IP address.) The client identifier, representing the application user, is available in user session information and can also be accessed within an application context (using the USERENV naming context), thus enabling applications to use Virtual Private Database to limit user access, even if the application users are not known to the database. Applications can set up and reuse sessions, while still being able to keep track of the "application user" in the session.
Application user proxy authentication, available in JDBC-OCI, provides the benefits of connection pooling without the overhead of setting up and managing separate user sessions (even "lightweight" ones), and enables even those applications whose users are unknown to the database to utilize Virtual Private Database. Application user proxy authentication is thus particularly valuable in eBusiness applications with thousands of users, as it supports data access control by user while meeting user scalability requirements.
Application context facilitates the implementation of fine-grained access control. It enables you to implement security policies with functions and then associate those security policies with applications. Each application can have its own application-specific context. Users are not permitted to arbitrarily change their context (for example, through SQL*Plus).
Application contexts permit flexible, parameter-based access control, based on attributes of interest to an application. For example, context attributes for a human resources application could include "position", "organizational unit", and "country" while attributes for an order-entry control might be "customer number" and "sales region".
Note that enterprise user security requires Oracle Advanced Security. This feature also supports Oracle Label Security labels and privileges.
Most applications contain information about the basis on which access is to be limited. In an order entry application, for example, customers should be limited to access their own orders (ORDER_NUMBER) and customer number (CUSTOMER_NUMBER). Application context is an underlying database feature that enables you to define, set, and access attributes that an application can use to enforce access control. You can securely store such user attributes as a user name, employee number, the set of books she is authorized to access, and her position in the management hierarchy. You can then retrieve that information later in the session and use it for fine-grained access control.
Application contexts can be initialized in four different ways:
The application context feature was introduced in Oracle8i. Within a local database environment, attribute values can be initialized from a user's session information. Each application can have its own context with its own attributes.
This feature lets you specify a special type of namespace that accepts initialization of attribute values from external resources. This enhances performance and enables the automatic propagation of attributes from one session to the other. Many applications store attributes used for fine-grained access control within a database metadata table that they use for access control. For example, an EMPLOYEES table could include cost center, title, signing authority, and other information useful for fine-grained access control. However, many organizations centralize user information and user management in an LDAP-based directory such as Oracle Internet Directory. These organizations also wish to centralize the information about users that is used for access control. Application context attributes can be stored in the directory and assigned to one or more enterprise users. They can be retrieved automatically upon login for an enterprise user, and used to initialize an application context.
This feature provides a centralized location to store the user's application context, enabling applications to set up the user's contexts during initialization based upon the user's identity. In particular, it supports Oracle Label Security labels and privileges. This feature makes it much easier for the administrator to manage contexts for large numbers of users and databases.
Application context initialized globally utilizes the Lightweight Directory Access Protocol (LDAP), which stores a list of users to which this application is assigned. Oracle can use Oracle Internet Directory as the directory service for authentication and authorization of enterprise users.
Global application context can be shared among trusted sessions. In addition to driving the enforcement of the fine-grained access control policies, applications (especially middle-tier products) can use this support to manage application attributes securely and globally.
Many web-based applications use connection pooling to achieve high scalability and thereby support hundreds of thousands of users. These applications set up and reuse connections instead of having different sessions for each user. For example, web user Jane and Ajit connect to a middle tier application, which establishes a session in the database used by the application on behalf of both users. The application is responsible for switching the username on the connection, so that, at any given time, it is either Jane or Ajit using the session.
In Oracle Enterprise Edition, Oracle9i's Virtual Private Database (VPD) capabilities facilitate connection pooling by enabling multiple connections to access one or more global application contexts, instead of setting up an application context for each user session. Global application contexts provide additional flexibility for web-based applications to use Virtual Private Database, as well as enhanced performance through reuse of common application contexts among multiple sessions instead of setting up application contexts for each session.
Application user proxy authentication can be used with global application context for additional flexibility and high performance in building eBusiness applications. For example, suppose a web-based application that provides information to business partners has three types of users: Gold, Silver, and Bronze, representing different levels of information available. Instead of each user having his own session--with individual application contexts--set up, the application could set up global application contexts for Gold, Silver or Bronze and use the client identifier to point the session at the correct context, in order to retrieve the appropriate type of data. The application need only initialize the three global contexts once, and use the client identifier to access the correct application context to limit data access.
By providing deep data protection, Internet-scale security, and security mechanisms specifically targeted for hosting applications and exchanges, Oracle Enterprise Edition is an ideal platform on which to build and deploy eBusiness applications. It contains all of the powerful features of Oracle Standard Edition, and more. This section includes:
For a thorough discussion of these features, see the Oracle documentation set.
EBusiness depends on providing customers, partners, and employees with access to information, in a way that is controlled and secure. Oracle addresses eBusiness security challenges through deep data protection, internet-scale security, and secure hosting and data exchange.
Deep data protection, ensuring well-formed, comprehensive security from client to application server to data server, as well as throughout the layers of an application.
Deploying eBusiness systems on the Internet increases risk. Among the best ways to mitigate security risk is to provide multiple layers of security mechanisms, so that failure of a single mechanism does not result in compromise of critical information. We refer to this concept as deep data protection; Oracle provides it through Virtual Private Database (VPD), Oracle Label Security, selective data encryption, and extensive auditing.
Internet-scale security enables user and privilege management to scale to hundreds of thousands of users accessing data. Oracle Enterprise Edition is the foundation for the Oracle Advanced Security features of user management, PKI integration, and directory-based privilege management.
Security mechanisms must scale to Internet size--support many thousands or millions of users--and still be practical to administer. Oracle provides a number of security features tailored to building Internet-scale applications, including proxy authentication, support for Internet standards such as Secure Sockets Layer (SSL) and relevant public key infrastructure (PKI) standards, Java security, and enterprise user security.
Secure hosting and data exchange enable economical, secure partitioning of data access by customer or by user, while supporting secure data sharing among communities of interest. Oracle Enterprise Edition is the foundation for Virtual Private Database technology, for the Oracle Advanced Security features of public key infrastructure (PKI) and enterprise user security, and for Oracle Label Security.
Each database application can have its own security policies. It can have its own privileges, and one or more database roles that provide different levels of security when executing the application. The database roles can be granted to user roles, or directly to specific usernames.
Applications that potentially permit unrestricted SQL statement execution (through tools such as SQL*Plus) also can have security policies that prevent malicious access to confidential or important schema objects. In this way you can ensure that users do not misuse their roles and privileges when they are not actually using the application.
Oracle Enterprise Edition provides row-level access control through its Virtual Private Database (VPD) technology, which is available only from Oracle Corporation. In addition, it supports the Oracle Label Security product, built on the Virtual Private Database toolkit, which adds label based access control.
This section describes:
| See Also:
For a complete discussion of application context, fine-grained access control, and VPD, see the following chapters in Oracle Database Security Guide: |
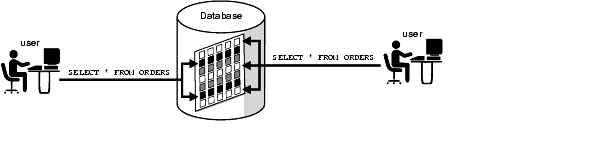
Oracle8i set a new standard in database security with the introduction of Virtual Private Database (VPD): server-enforced, fine-grained access control, together with secure application context, enabling multiple customers and partners to have secure direct access to mission-critical data. Within a single database, the Virtual Private Database enables data access control by user or by customer with the assurance of physical data separation. For Internet access, the Virtual Private Database can ensure that online banking customers see only their own orders. Web hosting companies can maintain multiple companies' data in the same Oracle database, while permitting each company to see only its own data.
Within the enterprise, the Virtual Private Database results in lower cost of ownership in deploying applications. Security can be built once, in the data server, rather than in each application that accesses data. Security is stronger, because it is enforced by the database, no matter how a user accesses data. Security is no longer bypassed when a user accesses an ad hoc query tool or new report writer. Virtual Private Database is key enabling technology for organizations building hosted, web-based applications, as well as for Oracle itself. Multiple Oracle applications, including Oracle SalesOnline.com and Oracle Portal, use VPD to enforce data separation for hosting.
Oracle9i's Virtual Private Database (VPD) feature provides fine-grained access control and uses application context. It secures data in the database by providing security at the row level, across all applications, by attaching a security policy directly to a table or view. In addition, VPD enables use of the following capabilities:
The Virtual Private Database is enabled by associating one or more security policies with tables or views. A security policy is a restriction on the type of access or view that a user can acquire. Direct or indirect access to a table with an attached security policy causes the database to consult a function implementing the policy. The policy function returns an access condition known as a predicate (a WHERE clause), which the database appends to the user's SQL statement, thus dynamically modifying the user's data access.
You can implement VPD by writing a stored procedure to append a SQL predicate to each SQL statement to control row level access for that statement. Your security policy then links the function to the desired schema and table. For example, if John Doe (who belongs to Department 10) inputs the statement SELECT * FROM emp, you can use VPD to tack on the clause WHERE DEPT = 10. In this way query modification is used to restrict data access to certain rows.
A secure application context enables access conditions to be based on virtually any attributes an application deems significant, such as organization, cost center, account number, or position. For example, an Web order entry system can enforce access based on customer number, and whether the user is a customer or a sales representative. In this way, customers can view their order status online (but only for their own orders), while sales representatives can view multiple orders, but only for the their own customers.
Text description of the illustration secov002.gif
The Virtual Private Database ensures that, no matter how a user gets to the data (through an application, a report writing tool, or SQL*Plus) the same strong access control policy is enforced. In this way, VPD can help banks ensure that customers see their own accounts (and nobody else's), that telecommunications firms can keep customer records safely segregated, and that human resources applications can support their complex rules of data access to employee records.
These fine-grained access control capabilities also apply when a synonym is used for the database name. Policy functions applied to a synonym can create the same constraints formerly imposed by creating views, without the costs in resources and processing that otherwise grow proportionately with the number of users.
Fine-grained access control enables you to build applications that enforce security policies at a low level of granularity. You can use it, for example, to restrict a customer who is accessing an Oracle server to see only his own account, a physician to see only the records of her own patients, or a manager to see only the records of employees who work for him.
The ability to partition security policy enforcement by application facilitates VPD deployment. For example, suppose both an Order Entry and Inventory application access the Orders table. The Order Entry application limits access based on customer number, while the Inventory application limits access based on part number. It is very useful to be able to partition fine-grained access control so that different security policies apply, depending upon which application is accessing the data. Otherwise, application developers of the respective Order Entry and Inventory applications have to agree upon a mutual policy, which may not be feasible or possible. Applications can thus have different security policies based upon their individual application needs.
Oracle enables partitioning of Virtual Private Database through policy groups and a driving application context. A driving application context securely determines which application is accessing data, and policy groups facilitate managing the policies that apply by application. Oracle also supports default policy groups, which always apply to data access. For example, an application "striped" for application hosting using a subscriber ID could have a default policy, "Subscriber," that always enforces data separation by subscriber, and additional policy groups for Inventory and Order Entry-based access, which apply depending on the particular application accessing data.
Applications may have differing user models, but still want to use VPD to limit access by user. Oracle provides a number of ways in which applications can enforce fine-grained access control by user, regardless of whether the user is a database user, or an application user unknown to the database.
For applications in which the application users are also database users, VPD enforcement is relatively simple; users connect to the database, and the application can set up application contexts for each session. Each session is initiated under a different username, so that it is simple to enforce different fine-grained access control conditions for "Jane" and "John". This is also possible with use of proxy authentication, since each "lightweight" session in JDBC-OCI is still a distinct database session, and can have its own application context. Since proxy authentication can be integrated with Enterprise User Security, user roles can be retrieved from Oracle Internet Directory, as well as other attributes that can be used for VPD enforcement.
For applications in which a single user (such as OneBigApplicationUser) connects to the database on behalf of all users, fine-grained access control by user is still possible. An application developer can create a context attribute to represent the application user (such as "realuser"). While all database sessions (and thus all audit records) are initiated as OneBigApplicationUser, each session can nonetheless have attributes that vary, depending on who the "real user" is. This model works best for applications with a limited number of users where there is no requirement for session reuse. Of course, each session--from the database standpoint--is created as the same database user, so that the ability to use roles, database auditing, and so on, is greatly diminished for reasons previously enumerated.
Oracle offers improved management of VPD policies through Oracle Policy Manager, an easy-to-use graphical user interface (GUI) accessed through Oracle Enterprise Manager. Developers can use Oracle Policy Manager to apply security policies to schema objects, such as tables and views, as well as creating application contexts, thus making VPD much easier to develop and manage. Oracle Policy Manager is also the administration tool for Oracle Label Security, a VPD-based product that provides label-based access to data. Oracle Label Security is thus a generic solution to the problem of fine grained data access control.
This feature, unique to Oracle, enables you to base use of roles on user-defined criteria. A secure application role is a role that is implemented by a package. For example, you could write a package permitting use of a role by a user connecting only from a particular IP address, or accessing the database only through a particular middle tier.
In three-tier systems using proxy authentication, the package can validate that the user session was created by a middle tier, and thus that the user is accessing the database through the correct application. The secure application role can also ensure that a user connecting directly to the database is not able to access any data. A secure application role can enforce other security conditions, as well; for example, the user may not be permitted to access especially sensitive human resources data from the Internet.
A secure application role enhances the native strong authentication and fine-grained access control of the database to prevent users from assuming any privileges unless the correct access conditions are met. Secure application role solves a very difficult security issue and supports secure web-based application data access.
Oracle expands upon the existing robust, granular auditing capabilities of the database by introducing extensible, fine-grained auditing. Fine-grained auditing enables organizations to hone their auditing capabilities to capture and identify particular, specific data access of concern. In addition to providing more granular, targeted audit information, such as detecting misuse of legitimate access, fine-grained auditing can also serve as an intrusion detection system for the Oracle database itself.
Fine-grained auditing enables organizations to define audit policies, which specify the data access conditions that trigger the audit event, and use a flexible event handler to notify administrators that the triggering event has occurred. For example, an organization may permit HR clerks to access employee salary information, but audits access when salaries greater than $500K are accessed. The audit policy "where SALARY > 500000" is applied to the EMPLOYEES table through an audit policy interface (a PL/SQL package named DBMS_FGA).
For additional flexibility in implementation, organizations can employ a user-defined function to determine the policy condition, and identify a relevant column for auditing. For example, the function could permit unaudited access to any salary as long as the user is accessing data within the intranet, but audit access to executive-level salaries when they are accessed from the Internet. An audit column helps reduce the instances of false or unnecessary audit records, because the audit need only be triggered when a particular column is referenced in the query. For example, an organization may only wish to audit executive salary access when an employee name is accessed, because accessing salary information alone is not meaningful unless an HR clerk also selects the corresponding employee name.
Upon a triggering audit event, Oracle captures the exact SQL text of the statement the user executed in audit tables, along with additional information such as the user executing the query, a timestamp, and so on. In conjunction with other database features such as LogMiner, fine-grained auditing can be used to re-create the exact records returned to a user. This may be especially important to organizations that have especially sensitive information they wish to share, for which they require strict accountability. For example, many law enforcement organizations at the international, federal, state and local level are increasingly becoming "eBusinesses" by sharing information among themselves, yet it is more important than ever that they audit access to sensitive information, such as informant data, to know who accessed what exact data.
The event handler provides organizations with flexibility in determining how to handle a triggering audit event. A triggering audit event could be written into a special audit table for further analysis, or could activate a pager for the security administrator. The event handler enables organizations to fine-tune their audit response to appropriate levels of escalation.
With Oracle, Oracle customers are not only able to preserve the identity of the real client over the middle tier and enforce "least privilege" through a middle tier, but can also audit actions taken on behalf of the user by the middle tier. Oracle audit records capture both the logged-in user (that is, the middle tier) who initiated the connection, and the user on whose behalf an action is taken.
Oracle contains a Java security implementation in the server. The Java virtual machine (JVM) is the Java interpreter that converts the compiled Java bytecode into the machine language of the platform and runs it. JVMs can run on a client, in a browser, in a middle tier, on a Web, on an application server such as Oracle Application Server, or in a database server such as Oracle.
In the Oracle JVM implementation, the right to execute code in classes is controlled by execute privileges on the classes themselves. This is the same database privilege as execute privilege on a PL/SQL package, and is managed in the same way.
The Oracle JVM starts with the class java.lang.SecurityManager installed. The Oracle database is based on the Java Developer's Kit 1.2 release from Sun Microsystems, and implements the security features of that release. In this implementation, permissions are controlled by the contents of a database table. The table is normally managed by PL/SQL procedures (and Java methods). The table can be used to grant permissions to either users or roles, and the "code source" of a class is identified with the user in whose schema the class has been loaded. Specific Oracle permissions control the right to update the table and perform other security sensitive operations.
Oracle Advanced Security is the value-added Internet security bundle for Oracle. Its functionality falls into three categories: network security services, enterprise user security, and public key infrastructure (PKI). The features of this product are described in the following sections:
Oracle Advanced Security bundles security services for Oracle. It is provided as a separately priced option that may be purchased along with Oracle Enterprise Edition.
Although installed by default, Oracle Advanced Security is a separately priced option to Oracle Enterprise Edition, and must be purchased when used. This licensing requirement also affects customers wishing to use security features in combination with Java Beans (EJB over IIOP/SSL) or database enterprise users with Oracle Net/SSL. The exclusive exception is an HTTPS (HTTP/SSL) connection to the RDBMS, which does not require an Oracle Advanced Security license.
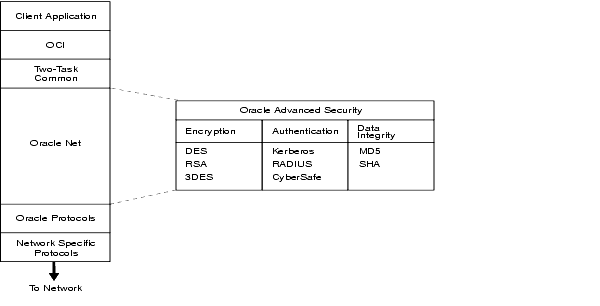
Figure 9-2 shows the Oracle Advanced Security architecture within an Oracle networking environment.
Text description of the illustration ano81013.gif
Oracle Advanced Security supports authentication through adapters that are very much like the existing Oracle protocol adapters.
| See Also:
for more information about stack communications in an Oracle networking environment, see Oracle Net Services Administrator's Guide |
Oracle Advanced Security provides several methods of protecting the privacy of data transmissions.
Oracle Advanced Security ensures data privacy by encrypting network traffic in order to prevent anyone from reading the data during transmission.
Oracle Advanced Security provides several industry-standard encryption and checksumming algorithms that can be selected based on the particular requirements of your system. Selection of the network encryption method offers varying levels of security and performance for different types of data transfers.
Note that the strength of cryptosystems depends on key management. Oracle Advanced Security uses the public-key based Diffie-Hellman key negotiation algorithm to perform secure key distribution for both encryption and data integrity. When encryption is used to protect the security of encrypted data, keys should be changed frequently to minimize the effects of a compromised key. For this reason, the Oracle Advanced Security key management facility changes the session key with every session. With Oracle Advanced Security, Diffie-Hellman Key Exchange is automatic, eliminating administration issues associated with encryption systems.
Prior versions of Oracle Advanced Security provided three editions: Domestic, Upgrade, and Export--each with different encryption key lengths. Release 9.0.1 now contains a full complement of the available encryption algorithms and key lengths for Oracle customers worldwide, previously only available in the U.S. Domestic edition. Users deploying prior versions of the product can obtain the U.S. Domestic edition for a specific product release.
Oracle Advanced Security comes out of the box with industry-standard algorithms and a FIPS-compliant implementation of cryptography, which help to simplify the often difficult task of implementing encryption. The following industry-standard encryption algorithms are supported:
Oracle Advanced Security hides the complexity of key management and encryption from the administrator and the users. Users need only perform a few simple steps to configure Oracle Advanced Security encryption. You can either use the Oracle Net Manager graphical user interface tool to select encryption algorithms, or else manually set six sqlnet.ora parameters. Once configured, the encryption is transparent to users.
Very little overhead is associated with Oracle Advanced Security encryption. Performance varies (depending on the operating system, the encryption algorithm chosen, and other factors); however, performance tests show a degradation of approximately one-tenth of a second.
Oracle Advanced Security ensures data integrity with sequenced, cryptographic checksums. To ensure that data has not been modified, deleted, or replayed during transmission, Oracle Advanced Security optionally generates a cryptographically secure message digest--through cryptographic checksums using the MD5 algorithm--and includes it with each packet sent across the network. Alternatively, Oracle Advanced Security can use SHA-1 (with SSL). Data integrity algorithms add little overhead, and protect against data modification attacks, deleted packets, and replay attacks.
Oracle Advanced Security provides SSL encryption capabilities, as described in this section.
The Oracle Advanced Security SSL feature can be used to secure communications between any client and any server. This includes data in Oracle Net Services, LDAP, JDBC-OCI, and IIOP format. SSL encryption provides users with an alternative to the native Oracle Net Services encryption protocol that is supported in Oracle Advanced Security. A benefit of SSL is that it is a de facto Internet standard, and can be used with clients that use protocols other than Oracle Net Services.
SSL support in Oracle Advanced Security encrypts network traffic and provides integrity checking, authenticates Oracle clients and servers, and brings public key-based single sign-on to the Oracle environment. SSL provides encryption and data integrity through the use of cipher suites, which are sets of authentication, encryption, and data integrity types. The client and server each have a list of cipher suites they support (such as RSA for authentication, with 3DES for encryption and SHA-1 for data integrity). They negotiate which one is to be used during connection.
The SSL feature of Oracle Advanced Security permits the use of the Secure Hash Algorithm (SHA) as well as MD5. SHA is slightly slower than MD5, but produces a larger message digest to make it more secure against brute-force collision and inversion attacks.
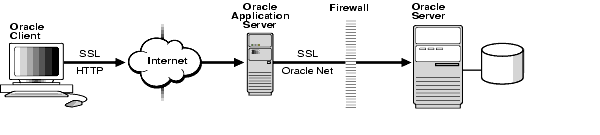
Oracle Application Server supports SSL encryption between thin clients and the Oracle Application Server, as well as between Oracle Application Server and Oracle Data Server.
Text description of the illustration secov001.gif
| See Also:
"Secure Sockets Layer (SSL) Protocol" "Secure Sockets Layer Authentication and X.509v3 Digital Certificates" |
Sun Microsystems defined the Java Database Connectivity (JDBC) standard, and Oracle Corporation, as an individual provider, implements and extends the standard with its own JDBC drivers. Oracle offers 4 kinds of JDBC driver:
Since the JDBC-OCI driver uses the full Oracle Net Services communications stack on both client and server, it can take advantage of existing Oracle Advanced Security encryption and authentication mechanisms. In Oracle, proxy authentication has been extended to Java Database Connectivity (JDBC-OCI), which enables a middle tier server to access the Oracle database on behalf of a client user by establishing a lightweight session for the user.
Because the thin JDBC driver is designed to be used with downloadable applets used over the Internet, Oracle includes a 100% Java implementation of Oracle Advanced Security encryption and integrity algorithms for use with thin clients. Several benefits enable eBusinesses deploying Oracle and other components to securely transmit a variety of information over a variety of channels:
The Oracle JDBC Thin driver implements the Oracle password protocol for authentication. It does not support Oracle Advanced Security SSL implementation, nor does it support third party authentication features such as RADIUS or Kerberos. The Oracle JDBC-OCI driver supports all Oracle Advanced Security features.
Oracle Advanced Security continues to encrypt and provide integrity checking of Oracle Net Services traffic between Oracle Net Services clients and Oracle servers using algorithms written in C. The Oracle Advanced Security Java implementation for Thin JDBC provides Java versions of the following encryption algorithms:
On the server, the negotiation of algorithms and the generation of keys function exactly the same as Oracle Advanced Security Oracle Net Services encryption, thus enabling backward and forward compatibility of clients and servers. On the clients, the algorithm negotiation and key generation occur in exactly the same manner as C-based Oracle Advanced Security encryption. The client and server negotiate encryption algorithms, generate random numbers, use Diffie-Hellman to exchange session keys, and use the Oracle Password Protocol, in the same manner as traditional Oracle Net Services clients. Thin JDBC contains a complete implementation of a Oracle Net Services client in pure Java. Consistent with other encryption implementations, the Java implementation of Oracle Advanced Security prevents access to the cryptographic algorithms, makes it impossible to double encrypt data, and encrypts data as it passes through the network. Users cannot alter the keyspace nor alter the encryption algorithms themselves.
Oracle Java SSL is a commercial-grade implementation of Java Secure Socket Extension (JSSE). In order to create a secure, fast implementation of SSL, Oracle Java SSL uses native code to improve the performance of critical components. In addition to the functionality included in the JSSE specifications, Oracle Java SSL supports the following:
Oracle Advanced Security provides enhanced user authentication through several third-party authentication services, and through the use of SSL with digital certificates. Many of these options use centralized authentication, which can give you high confidence in the identity of users, clients, and servers in distributed environments. It also provides for enhanced authentication by integrating technologies such as token cards to prove users' identities. User authentication, a function of Oracle9i, is significantly enhanced by using the authentication methods supported by Oracle Advanced Security.
Supported authentication methods include:
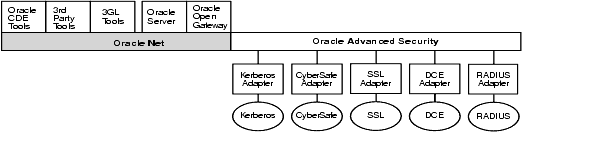
Figure 9-4 shows some of the strong authentication components of Oracle Advanced Security. The authentication adapters integrate below the Oracle Net Services interface and permit existing applications to take advantage of new authentication systems transparently, without any changes to the application.
Text description of the illustration ano81005.gif
Oracle provides a public key infrastructure (PKI) for using public keys and certificates. This section summarizes the Oracle PKI authentication capabilities.
Standard PKI Support in Oracle Advanced Security
Oracle supports standard X.509 version 3 certificates and relevant Public Key Certificate Standards (PKCS) for certificate request and installation. This enables users to request certificates from any certificate authority (CA) that also supports these standards. It also enables users to install trusted root certificates from their choice of CAs, enabling the server to recognize and validate certificates issued by those CAs. Oracle works with leading PKI service and product vendors, including VeriSign and Baltimore Technologies, to ensure that their CA trusted roots are pre-installed in Oracle, enabling customers to use certificates from those vendors to authenticate to Oracle9i out-of-the-box.Secure Sockets Layer (SSL) Authentication in Oracle Advanced Security
Oracle Advanced Security SSL can be used to authenticate:
Anonymous, server-only, and client/server authentication by X.509 certificates are supported.
SSL features can be used by themselves or in combination with other authentication methods supported by Oracle Advanced Security. For example, SSL can be used with Kerberos, using the encryption provided by SSL in combination with the Kerberos authentication method.
Users and administrators use Oracle Wallet Manager to manage digital certificates for use with SSL. Oracle Wallet Manager gives users and database administrators control over the contents of their wallets. The administrator can centrally manage wallets on an LDAP-compliant directory. Oracle Enterprise Login Assistant, an easy-to-use tool, is provided for end users to open the wallet and perform the login over SSL. This tool enables users to achieve single sign-on, simply and transparently, using certificates for authentication. The wallet and management tools are used together to securely store and manage certificates, private keys, and requests to certificate server.
Entrust/PKI Support in Oracle Advanced Security
Oracle Advanced Security enables customers of both Oracle Corporation and Entrust Technologies, Inc. to incorporate Entrust-based single sign-on into their Oracle applications. By integrating with Entrust/PKI, Oracle enhances its ability to provide X.509-based single sign-on to large customers who require the extensive key management, certificate revocation, and other features that Entrust provides.
Oracle Advanced Security supports Entrust Profile, which is the Entrust mechanism for storage of certificates and private keys and for secure credential management. Instead of accessing user credentials (private key and certificate) from an Oracle wallet, Oracle Advanced Security can access a user's Entrust Profile for authentication and single sign-on. Entrust integration requires Entrust Authority 5.
Oracle Advanced Security support for Kerberos and CyberSafe provides the benefits of single sign-on and centralized authentication of Oracle users.
|
Note: Oracle authentication for Kerberos provides database link authentication (also called proxy authentication). CyberSafe does not support proxy authentication. |
RADIUS (the Remote Authentication Dial-In User Service) support provides two major benefits for Oracle customers. First, it enables support for authentication technologies including token cards, smart cards, and challenge-response. Second, it readily integrates into existing systems by making the Oracle data server a RADIUS client, thus capitalizing on the infrastructure and investment that organizations have already made.
With RADIUS you can choose virtually any mechanism available to authenticate network users. Many token and smart card manufacturers support RADIUS, and any RADIUS-compliant device can integrate with Oracle Advanced Security to authenticate Oracle users with little modification required by the authentication provider. Since many organizations have implemented RADIUS for remote access to their networks, Oracle easily integrates into existing systems and takes advantage of the investments that an organization has already made.
Any third party authentication vendor can implement the client graphical user interface by customizing the Java interface class that ships with Oracle Advanced Security. Products from the following vendors integrate with Oracle Advanced Security by means of the RADIUS interface:
Token card technologies enhance user authentication. Oracle Advanced Security supports SecurID tokens from RSA, which strengthen security through two-factor authentication: the user must know the PIN and have the SecurID electronic token card. In addition, RADIUS support in Oracle Advanced Security permits integration with a variety of token cards. Organizations can choose which token(s) they would like to use to protect networks from unauthorized use.
Oracle Advanced Security integrates with RADIUS-compliant smart cards, in order to authenticate Oracle users. Smart cards are becoming popular as strong security devices. Since they contain a processor, they can generate dynamic passwords. Because they have memory, they are useful for storing data such as a username, a certificate, or a medical record. Smart cards are being widely deployed, and organizations relying on them for proof of user identities can do so when users connect to Oracle.
A biometric device vendor who supports RADIUS can integrate with Oracle Advanced Security. The biometric device, deployed on clients or servers (or both) requiring strong authentication, provides user authentication based on a physical characteristic of an individual.
Distributed Computing Environment (DCE) integration enables users to transparently use Oracle tools and applications to access Oracle databases in a DCE environment. Oracle Advanced Security supports DCE 1.0 from OSF, on certain platforms, such as Solaris, Windows, HP, AIX.
You can integrate your Oracle network with any or all of the DCE services, which include security services, authentication and single sign-on, and mapping of Oracle roles to DCE groups for central authorization management.
Oracle Advanced Security minimizes maintenance of multiple passwords by supporting secure, single sign-on capabilities in a distributed environment. A user only needs to log on once a day, and can automatically connect to other services without having to give a user name and password again. This eliminates both the need for the user to remember and administer multiple passwords, and the time spent logging into multiple services. Single sign-on also simplifies management of user accounts and passwords for system administrators.
Centralized authentication makes single sign-on possible. Different configurations are supported:
Oracle Advanced Security is integrated with several different technologies to support single sign-on functionality. These include Kerberos, CyberSafe, and DCE.
Oracle Advanced Security provides SSL-based single sign-on and Entrust-based single sign-on for Oracle users by integrating with LDAP v3-compliant directory services. The combination of integrated directory services and the Oracle PKI implementation enable SSL-based single sign-on to Oracle9i databases. Single sign-on lets users be authenticated once, with subsequent connections relying on the user's digital certificate.
Enterprise User Security addresses user, administrative, and security challenges by centralizing storage and management of user-related information in an LDAP-compliant directory service. When an employee changes jobs in such an environment, the administrator need only modify information in one location--the directory--to make effective changes in multiple databases and systems. This centralization can substantially lower administrative costs while materially improving enterprise security.
This release extends Enterprise User Security support into three-tier environments. Oracle proxy authentication features enable:
Note that this combination applies to both SSL-authenticated and password-authenticated enterprise users.
This section describes:
Oracle Advanced Security enables two types of enterprise users: those authenticated by SSL, and those authenticated with passwords.
SSL-authenticated users benefit from single sign-on to Oracle using industry-standard, interoperable X.509 v3 certificates over Secure Sockets Layer v3.
Oracle Advanced Security also implements password-based authentication for enterprise users, eliminating the requirement for client-side wallets and most Secure Socket Layer (SSL) processing. (SSL is still required to secure connections between the database and Oracle Internet Directory.) Password-authenticated enterprise users can use the same password, securely stored in the LDAP-compliant directory, to authenticate to multiple databases. Administrators can manage both types of user within one directory.
With its reduced processing overhead, improved ease-of-use, and simplified setup and administration, password-authenticated enterprise users are particularly useful for large user communities accessing multiple applications. Oracle Advanced Security supports enterprise user logins with password-based authentication for all prior Oracle client versions. Furthermore, enterprise users can use a single enterprise username and password to connect to multiple databases, if desired.
Note that with single sign-on, the user needs to be authenticated only once. With single password functionality, by contrast, the user can employ the same password for many different databases, but she may need to enter the password multiple times.
Three graphical user interfaces are provided with Oracle Advanced Security. You can use these tools to administer large user communities accessing multiple applications, and to ease logins for users.
| See Also:
"Components of Oracle Public Key Infrastructure-Based Authentication", where these tools are described |
With shared schemas (formerly known as schema-independent users), multiple enterprise users can share a database schema. In this way, there is no need to create the same users in each database. The payoff for deploying the directory in this way is fewer user accounts. It enables application developers to integrate user accounts, and scales user management to the Internet.
Oracle Advanced Security provides a new type of database link for SSL-enabled databases and enterprise users. Current user database links enable the user to connect as the procedure owner (or connected user) to the next database. The current user can access the procedure owner's tables in the next database.
They provide SSL mutual authentication between servers. Databases can trust one another for access control and other things. To use database links, databases must have implemented enterprise users and SSL. Database links used with SSL implemented with the Distributed_Trust_Admin package permits finer-grained control by the DBA.
The Oracle Advanced Security licence includes use of Oracle Internet Directory for storage of enterprise users, their passwords, their Oracle wallets, and their enterprise roles. In conjunction with other components of Oracle Advanced Security, Oracle Internet Directory enables you to accomplish centralized user management and authorization. Oracle Enterprise Security Manager is provided to create user entries in the directory, and manage authorizations for those users.
Oracle Advanced Security also supports the Microsoft Active Directory.
Oracle offers a variety of choices for implementing security, and the public key infrastructure (PKI) approach is just one of those choices. PKI is an emerging means of achieving security and single sign-on, adding extra value to the Oracle Advanced Security option. For example, to use RSA RC4 encryption, you can use Oracle Advanced Security for its native encryption component, or for SSL-based encryption. You can choose between a variety of authentication methods, including passwords, smart cards, and X.509 certificates. This section describes:
The Oracle PKI implementation establishes a secure information exchange, in compliance with the industry-standard specifications for PKI-related components. It incorporates a whole suite of products and features, as described in this section.
This protocol uses public key cryptography to provide authentication, secure session key management, encryption, and data integrity.
Oracle Call Interface (OCI) and PL/SQL functions are used to sign user-specified data using a private key and certificate, and to verify the signature on data using a trusted certificate.
A trusted certificate is a third-party identity that is trusted. The trust is used when an identity is being validated as the entity it claims to be. Typically, the certificate authorities you trust issue user certificates. If there are several levels of trusted certificates, a trusted certificate at a lower level in the certificate chain does not need to have all its higher level certificates re-verified. Oracle Advanced Security automatically installs trusted certificates from VeriSign, RSA, Entrust, and GTE CyberTrust.
Such a certificate is created when an entity's public key is signed by a trusted entity (a trusted Certificate Authority outside of Oracle). The certificate contains the identity of the user or service, a public key, and other information used to enable authentication. It ensures that the entity's information is correct and that the public key belongs to the entity. The certificate is loaded into an Oracle wallet to enable authentication.
An Oracle wallet is a container in which certificates and trusted certificates are stored and managed, such that there is no need for real time checking with the certificate authority. These data structures securely store a user private key, a user certificate, and a set of trusted certificates (the list of root certificates that the user trusts).
This is a Java-based application that security administrators use to manage public-key security credentials on both Oracle clients and database servers. It creates an Oracle wallet that can be opened using the Oracle Enterprise Login Assistant.
Oracle Wallet Manager creates a public-private key pair and manages credentials for a user. It issues PKCS#10 certificate requests to the certificate authority, and installs the certificate in the wallet. It ships with trusted certificates from VeriSign, RSA, and GTE CyberTrust, and can use a site's own in-house certificate authority.
Oracle Enterprise Login Assistant is a Java-based tool for opening and closing a user wallet in order to enable or disable secure SSL-based communications for an application. It provides single sign-on capability for SSL-authenticated users. Further, it provides the benefit of strong authentication as well as single sign-on in either a client/server or three-tier environment. Enterprise users authenticating with passwords also use it to change their passwords in a database or a directory.
This LDAP v3-compliant directory, built on the Oracle database, helps to enable PKI-based single sign-on. It enables you to securely manage the user and system configuration environment, including security attributes and privileges, for users authenticated using X.509 certificates. Oracle Internet Directory enforces attribute-level access control, enabling the directory to restrict read, write, or update privileges on specific attributes to specific named users (for example, an enterprise security administrator). It also supports protection and authentication of directory queries and responses through SSL encryption.
Oracle Enterprise Security Manager is the graphical user interface used to centrally administer enterprise users and enterprise roles, in an LDAP directory. Database administrators can use this tool to perform a variety of tasks, including the following:
Oracle Enterprise Security Manager launches out of Oracle Enterprise Manager. It scales to tens of thousands of users, and enables you to manage thousands of databases in various domains, as well as the users who connect to the databases.
Oracle expands PKI integration and interoperability through:
Oracle Advanced Security supports X.509 certificates stored in PKCS #12 containers, making the Oracle wallet interoperable with third party applications like Netscape Communicator 4.x and Microsoft Internet Explorer 5.x, and providing wallet portability across operating systems. Users who have existing PKI credentials may export them in PKCS#12 format and reuse them in Oracle Wallet Manager, and vice versa. PKCS#12 thus increases interoperability and reduces the cost of PKI deployment for organizations.
Oracle Enterprise Security Manager creates user wallets as part of the user enrollment process. The wallet is stored in Oracle Internet Directory, or other LDAP-compliant directory. Oracle Wallet Manager can upload wallets to--and retrieve them from--the LDAP directory.
Storing the wallet in a centralized LDAP-compliant directory supports user roaming, enabling users to access their credentials from multiple locations or devices, ensuring consistent and reliable user authentication, while providing centralized wallet management throughout the wallet life cycle.
In Oracle, Oracle Wallet Manager and Oracle Enterprise Login Assistant support multiple certificates for each wallet, including:
Oracle Wallet Manager supports multiple certificates for a single digital entity in a persona--with multiple private key pairs in a persona (each private key can match only one certificate). This enables consolidation of and more secure management of users' PKI credentials.
The private keys associated with X.509 certificates require strong encryption, over secure channels. Oracle replaces DES encryption with 3-key triple DES (3DES), which is a substantially stronger encryption algorithm and provides superior security for Oracle wallets.
As the public key infrastructure is deployed more frequently to secure such applications as email and electronic commerce, PKI is one of the most important investments companies are making. Because all clients, application servers and data servers can authenticate themselves to one another, PKI provides an important security infrastructure to a network.
SSL secures not only Oracle Net, but also other protocols such as IIOP (Internet Inter-ORB Protocol). By capitalizing on Java support, Oracle Advanced Security secures IIOP connections, giving Oracle the ability to work with thin clients and Enterprise JavaBeans (EJB).
Support for SSL in Oracle Advanced Security closes the loop for secure end-to-end communications between any client, a web server or application server, and any Oracle database. For example, w hen a user wants to connect to her financial institution to transfer funds, she must be able to verify beyond a doubt that she is providing sensitive information such as passwords and account numbers to the proper server. With SSL and public-key authentication, the server can verify its identity to her browser, and the client can identify itself to the server.
Now that organizations are implementing application servers and firewalls to protect their networks, the connection process expands. Using the same example, the financial information can be stored in an Oracle data server secured behind a firewall. The user connects to the database using SSL to connect over the Internet and to the application server, which passes the connect request over Oracle Net (still protected with SSL) through a firewall and to the secured Oracle server with her financial account information.
Certificates not only authenticate clients to servers, but they also authenticate servers to other servers. This expands the security of the entire system with secure database links for mutual authentication of servers. With SSL deployment, all clients and all servers, including database servers and application servers, have credentials that identify them to all other machines and services with which they communicate.
The complete package that Oracle delivers provides standards-based methods to prevent eavesdropping, tampering with, or forging messages sent over the network, while providing single sign-on and strong authentication of clients and servers in the network and over the Internet. A public key infrastructure paves the way for secure electronic commerce in the Information Age.
Oracle Label Security, an add-on security option for the Oracle Enterprise Edition, enables you to customize your own label-based access control policies. Oracle Policy Manager is a convenient graphical user interface provided with this product.
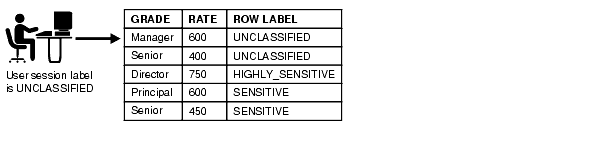
Text description of the illustration olsag008.gif
This product enables an administrator to add label based access control to the access mediation process when standard access controls are insufficient. Oracle Label Security is built on the Virtual Private Database toolkit and requires no programming whatsoever. It mediates access to rows in database tables based on a label contained in the row, a label associated with each database session, and Oracle Label Security privileges assigned to the session. Oracle Label Security delivers a data dictionary and administrative tools you can use to construct valid labels, set user label authorizations and privileges, and apply the resulting Oracle Label Security policy to tables and schemes.
The Oracle Virtual Private Database toolkit and Oracle Label Security provide very useful mechanisms for hosting and exchanges. Virtual Private Database provides fine grained access control within the database. It can be configured to keep data from different organizations separate within a single database instance, so that organizations can share database tables but only see data that pertains to them. This makes it ideal for hosting, since a system administrator for a hosting company can set up and configure a single version of each application for which they provide hosted services, but use Virtual Private Database on the underlying application tables to provide separate virtual applications instances for each hosted customer. This can substantially reduce the costs associated with hosting. Because hardware, database, and applications instances can be shared, the costs associated with hardware, as well as installation and configuration of software, are lower than if physically separate instances were required for each hosted customer.
Oracle Label Security is particularly useful for hosting environments in which access to information can be formalized by means of sensitivity levels, access categories, or user groups. For these environments, Oracle Label Security makes it easy for hosting companies to define and administer label-based security policies. Oracle Label Security provides particular advantages for exchanges, because the label-based access policies include automatic, easy-to-administer "group" access embedded within a data label that can support communities of interest.
The label-based access policies of Oracle Label Security are also ideal for enforcing privacy concerns of users accessing eBusiness applications. Many consumers are reluctant to purchase goods and services over the Internet because of privacy concerns. With Oracle Label Security, data can be labeled with an "opt out" provision for users who do not wish their data to be used for targeted marketing campaigns, or who do not wish their purchasing data to be sold. Data labels--and therefore users' privacy policies--remain with the data, making it easy to secure and enforce user privacy preferences across multiple applications.
Oracle Internet Directory is a directory service implemented as an application on the Oracle database. It enables retrieval of information about dispersed users and network resources. It combines Lightweight Directory Access Protocol (LDAP) Version 3, the open Internet standard directory access protocol, with the high performance, scalability, robustness, and availability of the Oracle Server.
Oracle Internet Directory is not itself a security product, but rather a technology for managing enterprise data very efficiently. It contributes to data security by supporting LDAP directory enterprise user security.
The Oracle platform has been designed to be LDAP-aware in numerous ways. The stringent security requirements of Oracle customers limits the choice of LDAP servers that are adequate to the task. In most cases, Oracle Internet Directory is the only LDAP server supported.
This section includes:
Oracle Internet Directory offers comprehensive and flexible support for directory access control. This includes entry level, attribute level, and prescriptive access control to provide varying levels of security to meet the specific needs of enterprise and service providers. An administrator can grant or control access to a specific directory object or to an entire directory subtree. Oracle Internet Directory implements three levels of user authentication: anonymous, password-based, and certificate-based using Secure Sockets Layer (SSL) Version 3 for authenticated access and data privacy.
In addition, Oracle Internet Directory provides many powerful features you can use in an enterprise or hosted environment to control access to application metadata--the information governing how applications behave and who can access them. To do this, you deploy the directory for administrative delegation. This deployment enables, for example, a global administrator to delegate to department administrators access to the metadata of applications in their departments. These department administrators can then control access to their department applications.
Oracle Internet Directory offers important benefits:
The Lightweight Directory Access Protocol (LDAP) has been incorporated into the Oracle Internet Directory. Oracle Internet Directory is probably the most scalable LDAP directory. It leverages the intrinsic scalability of the Oracle database, simplifying the management of hundreds of thousands of users. LDAP Naming, along with support for the Oracle Internet Directory centralized directory service, adds a new, unified naming mechanism for clients to use.
Oracle Internet Directory implements Version 3 of the Lightweight Directory Access Protocol (LDAP). This is the emerging Internet standard for directory services. It is based on the earlier ISO X.500 Directory Access Protocol (DAP) standard, but simplifies that standard considerably, enabling LDAP to be more efficient, straightforward, and easier to implement. LDAP is especially suited for deployment with Internet-centric, "thin-client" applications.
Each LDAP directory server instance looks like the configuration in Figure 9-6.
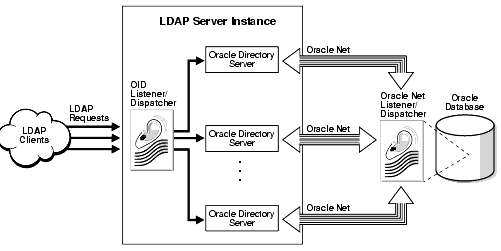
Text description of the illustration secov005.gif
Oracle Advanced Security can integrate with LDAP version 3-compliant directories. Your Oracle Advanced Security license entitles you to deploy Oracle Internet Directory for user management as well as authorization storage and retrieval.
An Oracle Internet Directory node is implemented as an application running on the Oracle server. To communicate with the database, which may be on the same platform or on a different one, the Oracle Internet Directory uses Oracle Net Services, the Oracle platform-independent database connectivity solution. This relationship is illustrated in Figure 9-7.
Text description of the illustration secov006.gif
This section describes enterprise user administration and shared schemas with Oracle Internet Directory.
Oracle Internet Directory supports attribute-level access control and optional strong user authentication through SSL, and can be configured so that only specific users who are strongly authenticated are permitted to update directory information about user privileges or access.
Enterprise roles are centrally-administered privilege sets, maintained in Oracle Internet Directory, or in directories from selected partners that meet Oracle security criteria. Enterprise roles enable strong, centralized authorization of users. Also, an administrator can add capabilities to enterprise roles (granted to multiple users) without having to update the authorizations of each user independently. Oracle Enterprise Security Manager provides one tool to centrally manage user definitions and assign roles, resulting in a lower cost of user administration throughout the enterprise. Another benefit of single station administration is that if security is easy to administer, organizations are more likely to implement strong security throughout the enterprise.
Oracle Internet Directory supports shared schemas, which extend the benefits of directory integration by enabling the database to delegate administration of user identity, as well as privilege, to the directory.
Oracle Net Services is a software layer that resides on the client and the Oracle database server. It is responsible for establishing and maintaining the connection between the client application and server, as well as exchanging messages between them using industry-standard protocols. This section includes:
Oracle Net Services is composed of Oracle Net, the listener, and Oracle Connection Manager. This section includes:
On the client side, applications communicate with Oracle Net Client to establish and maintain connections. Oracle Net Client, in turn, uses Oracle protocol support that is able to communicate with an industry-standard network protocol, such as TCP/IP, to communicate with the Oracle database server.
The Oracle database server side is similar to the client side. A network protocol sends client request information to an Oracle protocol support layer, which then sends information to Oracle Net. Oracle Net then communicates with the Oracle database server to process the client request. The one operation unique to the Oracle database server side is the act of receiving the initial connection through a process called the listener. The listener brokers a client request, handing off the request to the server.
Oracle Net uses Oracle protocol support to communicate with the following industry-standard network protocols:
Oracle Connection Manager is a software component that resides on its own computer, separate from a client or an Oracle database server. It proxies requests destined for the database server. You can also configure Oracle Connection Manager to multiplex sessions, control access, or convert protocols.
As a protocol converter, Oracle Connection Manager enables a client and an Oracle database server that have different networking protocols to communicate with each other. Oracle Advanced Security is fully supported by Oracle Connection Manager, making secure data transfer a reality across network protocol boundaries. Clients and a database server configured with different network protocols can securely share data with one another. To eliminate potential weak points in the network infrastructure and to maximize performance, Connection Manager passes encrypted data from protocol to protocol without the cost and exposure of decryption and re-encryption.
As an access control filter, Oracle Connection Manager controls access to Oracle databases. It can be configured to grant or deny clients access to a particular database service or a computer. By specifying filtering rules on source, destination, and database service name, you can permit or restrict specific clients access to a server.
In its session multiplexing role, Oracle Connection Manager funnels multiple sessions through a single transport protocol connection to a particular destination. This reduces the demand on resources needed to maintain multiple sessions between two processes by enabling the Oracle database server to use fewer connection end points for incoming requests. You can thus increase the total number of network sessions that a server can handle. To increase the number of concurrent users, multiple instances of Oracle Connection Manager can be installed.
When Oracle Connection Manager is run on the same computer as an application Web server, the application Web server can route multiple client sessions through Oracle Connection Manager to ensure that those sessions have continuous access to an Oracle database server. This functionality is especially useful for Web applications where session availability and response time are major concerns.
Firewalls can be implemented in two ways:
Oracle Connection Manager can be deployed as a firewall within an intranet. It can be configured to grant or deny client access to a particular database service or a computer. By specifying filtering rules, you can permit or restrict specific client access to a server, based on the following criteria:
Figure 9-8 shows an Oracle Connection Manager positioned between three Web clients and an Oracle database server. Oracle Connection Manager is configured to permit access to the first two Web clients and to deny access to the third. For this configuration to work, clients require the JDBC Thin driver.
Text description of the illustration net81082.gif
Oracle Corporation works with firewall vendors to incorporate key firewall technologies in its server products and thereby provide support for distributed database network traffic. Oracle Connection Manager functionality is offered by some firewall vendors through a software component called Oracle Net Firewall Proxy. A host computer, called an application gateway, runs the Oracle Connection Manager software.
Figure 9-9 shows an application gateway controlling traffic between internal and external networks and providing a single checkpoint for access control and auditing. As a result, unauthorized Internet hosts cannot directly access the database inside a corporation, but authorized users can still use Internet services outside the corporate network. This capability is critical in Internet environments to restrict remote access to sensitive data.
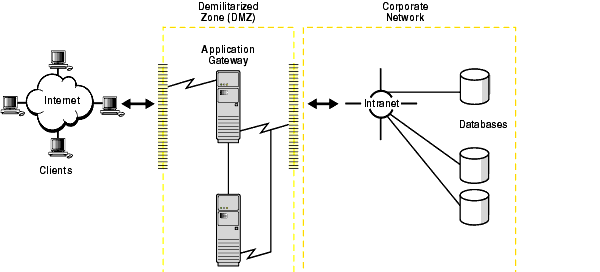
Text description of the illustration net81083.gif
Besides using Oracle Connection Manager to check for valid nodes, two Oracle Net Services protocol-specific parameters (TCP.EXCLUDED_NODES and TCP.INVITED_NODES) enable you to configure client access control to the database. In addition, you can use the parameter TCP.VALIDNODE_CHECKING to check for the TCP.INVITED_NODES and TCP.EXCLUDED_NODES to determine which clients to permit or deny access.
You can also use Virtual Private Database (or secure application roles) to limit access to the database from particular network nodes. Note that you would not want to make IP address a primary way of authenticating or authorizing users, since IP addresses can be spoofed. However, you can use IP address as an additional qualifier to limit data access for users whose authentication was separately established. For example, user Jane may have access to the EMP table, but company policy may dictate that she is not permitted to access EMP data unless she is inside the corporate intranet--perhaps even from a particular subnet for the HR department.
Both VPD and a secure application role can be used to limit access to data based on IP address. In the case of VPD, a policy function can access the IP address of the client connection using the USERENV naming context as follows:
SYS_CONTEXT('userenv', 'ip_address')
Further, the policy function can be defined to permit access to data only if the IP address is within the range of acceptable values (such as inside the corporate intranet, or within the range of addresses reserved for the HR department).
In the case of proxy authentication, in which the IP address of the client connection is the IP address of the application server that initiated the lightweight session, you can effectively force users to access the database only through the application server. Specifically, the VPD policy function can use the USERENV naming context
SYS_CONTEXT('userenv', 'ip_address')
to enforce that no records are returned unless the IP address matches that of the application server.
Note that this does not prohibit users from connecting directly to the database, as long as they are properly authenticated. Rather, it merely restricts the records returned to them. Using valid_node checking is actually a better general way to control user access, since it directly restricts connection to the database to particular IP addresses.
The secure application role can also use the USERENV naming context (that is, SYS_CONTEXT('userenv', 'ip_address')) to permit the enabling of roles only when connecting from a particular IP address.
Policies can be used on views, achieving a far lower cost in dictionary processing. Policies can also be used on synonyms, enabling applications that rely on synonyms to achieve better security by using VPD.
Oracle Application Server is a reliable, scalable, secure, middle-tier application server designed to support your evolution into an eBusiness. With this product, the technological complexity of assembling a complete middle-tier Internet infrastructure is managed for you. Oracle Application Server provides an infrastructure that can grow with your business. It can start small and support growing numbers of users and sophisticated functionality on your web sites.
This section introduces security features of Oracle Application Server, which includes components that provide a general framework for development and deployment of applications, such as the HTTP Server and Portal, and components that provide specific application services or functionality. This section focuses on the security services provided by the HTTP Server and Portal, since that is where the general security functionality in Oracle Application Server is implemented.
The Oracle HTTP Server is a web server based on Apache, an open source web server that is among the most widely adopted web server products. The Oracle HTTP Server extends Apache with a variety of standard and Oracle-unique enhancements (or "mods," as they are referred to in the Apache community). It provides a basic HTTP listener capability as well as the ability to support both static and dynamic web pages. In addition, it provides security services such as Secure Sockets Layer (SSL) encryption, and integration with the other Oracle Application Server components and products such as the Oracle database.
The Oracle Application Server provides a comprehensive set of security services. These include the ability to restrict or permit access to files and services based on the identity of users established by means of basic challenge/response operations, by means of client-supplied X.509 certificates, and by means of IP or hostname addresses. Confidentiality is provided by the SSL protocol, which is also used to present X.509 certificates to the HTTP Server. In addition, the HTTP Server provides logging and other facilities needed to detect and resolve intrusion attempts.
Oracle Portal is a key component of Oracle Corporation's product offering in the "Enterprise Portal" category. This is an emerging class of products that provide a gateway to business-related information on corporate intranets, in the same way that Internet portals are the gateway to content on the Internet.
Enterprise portals, as a both a consolidation and extension of existing market spaces, is a logical market for Oracle Corporation, which has a strong technology base, a wide range of applications that manage critical business data (ERP/CRM/BI), and a framework that leverages the technology to bring the applications together with other datastores on the Intranet (Oracle Portal). The functionality built into Oracle Portal provides a common framework across multiple Oracle products and applications. A customer who has purchased "portal enabled" Oracle products can easily extend them to other uses in an incremental fashion, as dictated by business needs and priorities.
An important security feature of Oracle Application Server is support for single sign-on (SSO) to web-based applications. There are a number of reasons why businesses are considering SSO. These include the increasing use of web-based eBusiness applications that companies are deploying for use by employees, customers and partners. Without SSO, each user must maintain a separate identity and password for each application they access. Maintaining multiple accounts and passwords for each user is insecure and expensive. This section describes:
The Oracle Web SSO technology provides single sign-on for web users. It is designed to work in a portal environment such as that provided by Oracle Application Server, where multiple web-based applications are accessible through the portal.
Two types of applications are supported by Web SSO. Partner applications are those that work within the SSO framework and rely on the SSO service for authentication of users. External applications continue to use their own usernames and passwords. The Oracle Web SSO approach is based on cookies, which are created both by partner applications and a centralized server called the Login Server.
The core of Oracle Corporation's SSO technology is the Login Server. This product provides web-based single sign-on and integration with legacy applications. With single sign-on, the Login Server authenticates users, and passes their identity securely to partner applications. The Login Server prompts users for a username and password when they access the system for the first time in a given time period (usually a day), and verifies the password presented by the user. Login Server SSO uses cookies, which are formatted pieces of information stored on a browser client by a web server. Cookies permit web servers to store and retrieve information about the client user, effectively maintaining client state information in the otherwise stateless web environment. Cookies are supported by all current browsers, although they can be disabled by the user (in which case Login Server will not provide SSO).
Oracle Login Server permits SSO usernames and passwords to be verified using Oracle Internet Directory. When a user submits an SSO username and password to the Login Server as part of the initial authentication, the Login Server performs an LDAP-bind against the Oracle Internet Directory using this username and password. If the LDAP-bind succeeds, the SSO username and password is considered to be verified.
PKI authentication is beginning to replace passwords in many applications. In web-based applications, PKI authentication is typically performed through an exchange of X.509 certificates, as part of a Secure Sockets Layer (SSL) session establishment. PKI by itself can be used to provide SSO, since a user with a certificate can authenticate to multiple applications without entering a password. In the future, users will be able to authenticate to the Login Server by means of PKI. This will provide SSO both to web-based applications supported by Login Server, and other PKI-enabled applications.
The Login Server provides SSO for web client access to web servers. Web servers are increasingly being deployed as the middle tier in a three tier architecture, where they provide access to a back-end tier database. It is desirable that users who access web applications that require access to the database not have to supply a database username and password for access to data stored there. Although the Login Server does not support non-web based applications, the Oracle database includes features specifically designed to support secure access to databases through three-tier architectures.
The Oracle strategy for SSO encompasses a variety of technologies. For the growing field of web-based applications, Oracle has developed an SSO framework and Login Server specifically designed to provide web SSO. The Oracle Web SSO approach has a number of benefits. It provides a framework for secure SSO from browser clients to web-based applications, including Oracle Applications and tools, through standard protocols. It supports both partner applications, which take full advantage of the SSO framework, as well external applications for support of legacy and third party products. It is well-integrated with the Oracle middle tier web portal product, Oracle Portal, and permits management of user information in an external directory, permitting integration with SSO technologies for other, non-Oracle applications. It will soon support PKI client authentication, which will enable PKI authentication to a wide range of web applications.